加密流量分类-实践4: 流量过滤
本文于 404 天之前发表,文中内容可能已经过时。
加密流量分类-实践4:流量过滤
- 炼丹的时候,经常需要过滤无关流量
- 论文的通常做法是将dns、icmp、arp、tcp握手报文删除
以下是给出我的代码,用wirshark前后对比pcap有效
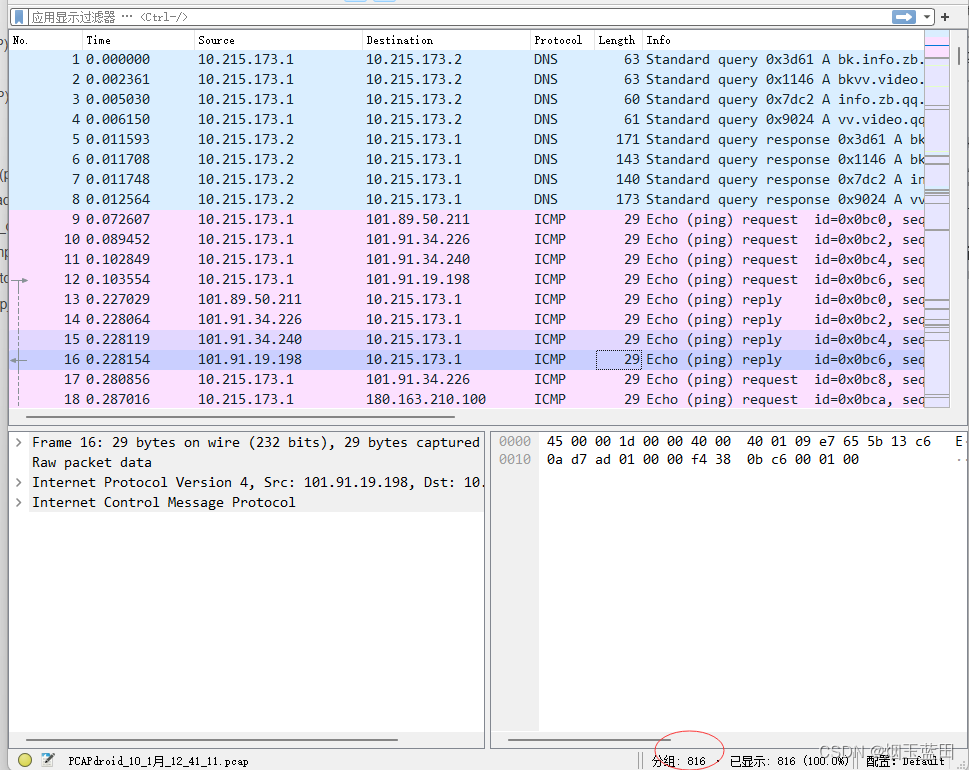
from scapy.all import * from scapy.layers.dns import DNS from scapy.layers.inet import ICMP, TCP from scapy.layers.l2 import ARP def remove_pcap_errors(file_path,new_path): """过滤的pcap与新的pcap不冲突""" packets = rdpcap(file_path) dns_cnt = 0 icmp_cnt = 0 arp_cnt = 0 tcp_flags = 0 new_packets = [] for packet in packets: if packet.haslayer(DNS): dns_cnt+=1 elif packet.haslayer(ICMP): icmp_cnt += 1 elif packet.haslayer(TCP) and (packet[TCP].flags.value==0x12 or packet[TCP].flags.value==0x02 or packet[TCP].flags.value==0x11): tcp_flags+=1 elif packet.haslayer(ARP): arp_cnt += 1 else: new_packets.append(packet) wrpcap(new_path, new_packets) print("dns:{}个".format(dns_cnt)) print("icmp:{}个".format(icmp_cnt)) print("tcp握手:{}个".format(tcp_flags)) print("arp包:{}个".format(arp_cnt))- 处理前:
-
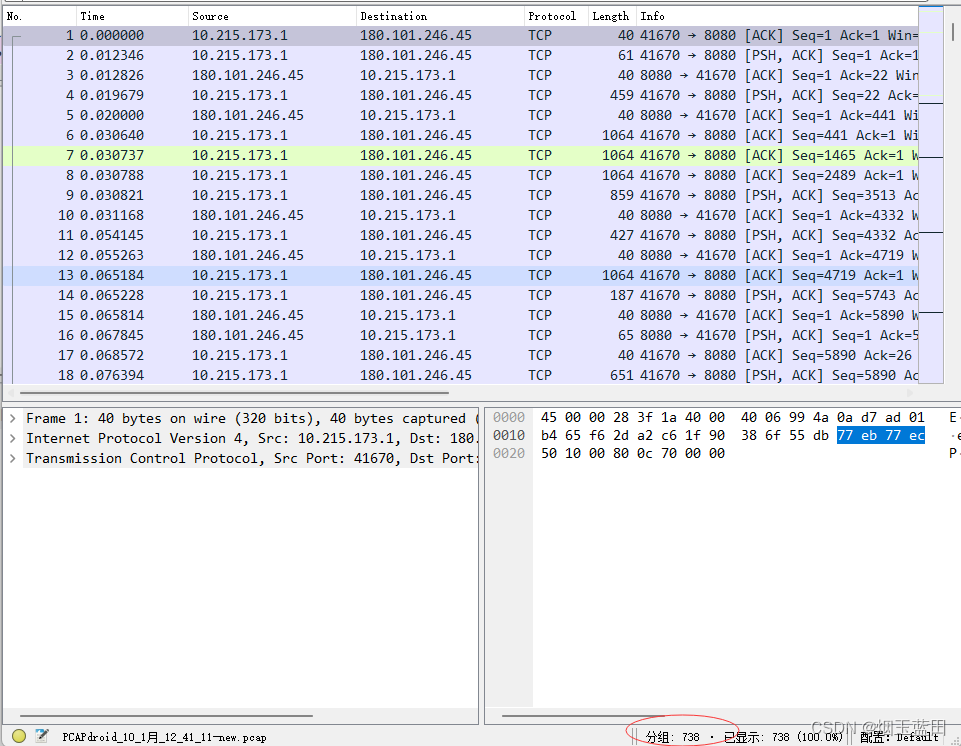
- 处理后:
-